Whitelist Security
Our solution uses application whitelisting for advanced malware prevention and detection, device authentication, Microsoft Office security, and more.
Stop responding to threats and start preventing them. Telesystem's Endpoint Protection solution is a comprehensive IT platform that effectively secures business users and data while making systems more productive and reliable.
Our proactive whitelist security stack seamlessly protects your organization from viruses, malware, and ransomware threats while optimizing your cyber infrastructure.
Our solution uses application whitelisting for advanced malware prevention and detection, device authentication, Microsoft Office security, and more.
Comprehensive RDP controls including the ability to enable and disable sessions, schedule remote access permissions, generate activity log reports, and authenticate devices for remote access.
Enjoy total automation of endpoint maintenance with powerful endpoint optimization for applications, Windows and network settings.
Remote access with multi-factor device authentication makes deployment, installation, access, and computer management easier than ever.
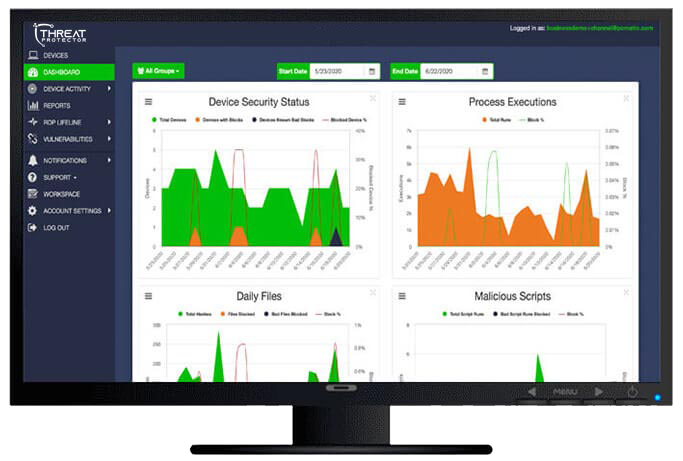
Our central dashboard provides system health at-a-glance, and key metrics such as CPU load, storage utilization and bandwidth-use, in one central location - along with device and session settings management.
Our Endpoint Protection solution has the world’s largest collection of hardware drivers, making it the fastest and simplest way to ensure all of your endpoints start fast and stay fast without the hassle of tracking down missing drivers.
We believe the most effective method for proactive detection is through application whitelisting. However, traditional whitelisting is difficult to deploy and even harder for IT staffs to manage.
Telesystem offers an alternative approach, with a globally automated whitelist managed by a team of professional malware researchers that automatically analyze unknown applications and categorize them globally.
3 Year Plan |
$3.00 |
2 Year Plan |
$5.00 |
1 Year Plan |
$6.00 |